Main Page: Difference between revisions
User890104 (talk | contribs) |
User890104 (talk | contribs) No edit summary |
||
| (14 intermediate revisions by 3 users not shown) | |||
| Line 1: | Line 1: | ||
__NOTOC__ | __NOTOC__ | ||
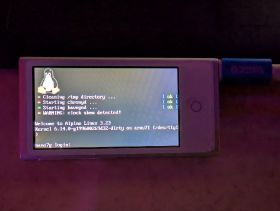
[[File:Photo 2025-12-27 20-36-24.jpg|280px|thumb|right|[[Linux]] 6.14.0 on [[Nano 7G]]]] | |||
[[File:EmCORE_Nano2G_Nano4G_Classic.jpg|280px|thumb|right|[[emCORE]] r779 on [[Nano 2G]], [[Nano 4G]] and [[Classic 2G]]]] | [[File:EmCORE_Nano2G_Nano4G_Classic.jpg|280px|thumb|right|[[emCORE]] r779 on [[Nano 2G]], [[Nano 4G]] and [[Classic 2G]]]] | ||
This is the wiki for the freemyipod project. Freemyipod is a project aimed at reverse-engineering non-iOS iPods (all models other than the Touch) and creating tools and documentation so that other people can port alternative firmwares to them such as [ | This is the wiki for the freemyipod project. Freemyipod is a project aimed at reverse-engineering non-iOS iPods (all models other than the Touch) and creating tools and documentation so that other people can port alternative firmwares to them such as [https://www.rockbox.org/ Rockbox] or [https://kernel.org/ Linux]. Freemyipod is a relaunch of [[Linux4nano]]. | ||
== FAQ == | == FAQ == | ||
=== What can I do with my | === What can I do with my [[Nano 2G]], [[Classic 6G]] or older iPods? === | ||
There's an upstream Rockbox port for these devices. Go use that. | There's an upstream Rockbox port for these devices. [https://www.rockbox.org/download/ Go use that]. | ||
=== What can I do with my | === What can I do with my [[Nano 3G]] or newer? === | ||
Not much (yet) unless you're an embedded developer :). | Not much (yet) unless you're an embedded developer :). | ||
On the | On the [[Nano 3G]], [[Nano 4G]] and [[Nano 5G]], we have a stable tethered exploit ([[wInd3x]]) which allows early, untethered and safe (no permanent modification) code execution. This in turn allows you to run [[U-Boot]] and an early [[Linux|Linux port]] or experiment with reverse-engineering/modifying the original firmware, [[retailOS]]. | ||
On the | On the [[Nano 6G]], [[Nano 7G]] and iPod shuffle (4th generation), a vulnerability in DFU_DNLOAD packet parsing code can be exploited with [[S5Late]]. It allows tethered code execution. | ||
On the [[Nano 6G]] and [[Nano 7G]], a font parsing vulnerability (CVE-2010-1797) can be exploited with [[ipod_sun]]. It allows untethered code execution. | |||
There's a set of earlier tooling ([[emCORE]]/[[emBIOS]]/[[iBugger]]) which was exploiting other vulnerabilities and was a lead-up to a port of Rockbox, but it's mostly abandoned. | There's a set of earlier tooling ([[emCORE]]/[[emBIOS]]/[[iBugger]]) which was exploiting other vulnerabilities and was a lead-up to a port of Rockbox, but it's mostly abandoned. | ||
| Line 23: | Line 26: | ||
==Updates== | ==Updates== | ||
* {{#dateformat:2024-12-16}} - [[S5Late]], a tethered iPod bootrom/DFU exploit for Nano 7G (and possibly Nano 6G), is released. | * {{#dateformat:2025-12-28}} - [[User:Hug0|Hug0]] made a lightning talk at 39C3 on [https://www.youtube.com/watch?v=FKHL1yyOKJc iPod Nano reverse engineering]. | ||
* {{#dateformat:2023-12-28}} - [[ipod_sun]], a tool that enables code execution on the | * {{#dateformat:2025-12-26}} - Some of us will be at 39C3 in Hamburg! Get in touch with [https://events.ccc.de/congress/2025/hub/en/user/q3k q3k] and/or [https://events.ccc.de/congress/2025/hub/en/user/slackware Slackware] if you're around! | ||
* {{#dateformat:2023-01-07}} - [https://social.hackerspace.pl/@q3k/109655916469636189 A preliminary U-Boot port to the Nano 5G has been developed.] | * {{#dateformat:2025-06-12}} - Some of us will be at GPN23 in Karlsruhe! [https://entropia.de/GPN23 More info here]. Let us know on IRC/Discord/Matrix if you're also there! | ||
* {{#dateformat:2022-01-04}} - The bootrom of | * {{#dateformat:2024-12-25}} - Some of us will be at 38C3 in Hamburg! [https://events.ccc.de/congress/2024/hub/en/project/ipod-nano-hacking-freemyipod/ Come say hi!] | ||
* {{#dateformat:2021-12-31}} - An exploit named wInd3x, which exploits the latest vulnerability, is being prepared for Nano 4G and Nano 5G. | * {{#dateformat:2024-12-16}} - [[S5Late]], a tethered iPod bootrom/DFU exploit for [[Nano 7G]] (and possibly [[Nano 6G]]), is released. | ||
* {{#dateformat:2021-12-27}} - A new vulnerability was discovered in | * {{#dateformat:2023-12-28}} - [[ipod_sun]], a tool that enables code execution on the [[Nano 6G]] and [[Nano 7G]], is released. | ||
* {{#dateformat:2023-01-07}} - [https://social.hackerspace.pl/@q3k/109655916469636189 A preliminary U-Boot port to the [[Nano 5G]] has been developed.] | |||
<!-- | |||
* {{#dateformat:2022-01-04}} - The bootrom of [[Nano 5G]] was successfully dumped, and is in the process of being reverse-engineered! | |||
* {{#dateformat:2021-12-31}} - An exploit named wInd3x, which exploits the latest vulnerability, is being prepared for [[Nano 4G]] and [[Nano 5G]]. | |||
* {{#dateformat:2021-12-27}} - A new vulnerability was discovered in [[Nano 4G]] and [[Nano 5G]] bootrom, which allows arbitrary code execution! | |||
* {{#dateformat:2018-08-25}} - The website software has been updated to MediaWiki 1.31 after about 2 months of downtime. | * {{#dateformat:2018-08-25}} - The website software has been updated to MediaWiki 1.31 after about 2 months of downtime. | ||
* {{#dateformat:2016-06-17}} - The freemyipod project is becoming deprecated, as parts of the code is slowly being integrated in Rockbox. It is likely that no future development on the freemyipod project will take place. Essential parts of emCORE helped building a Rockbox bootloader for iPod Classic, and any future development will take place in the Rockbox project. | * {{#dateformat:2016-06-17}} - The freemyipod project is becoming deprecated, as parts of the code is slowly being integrated in Rockbox. It is likely that no future development on the freemyipod project will take place. Essential parts of emCORE helped building a Rockbox bootloader for iPod Classic, and any future development will take place in the Rockbox project. | ||
* {{#dateformat:2014-03-26}} - A bug that prevented [[emCORE]] installations on certain Windows configurations (getting stuck on "Booting UBI file..."), has been finally fixed! If the installation has failed for you before, you can retry it using the updated version of our tool (use the iTunes method for now). | * {{#dateformat:2014-03-26}} - A bug that prevented [[emCORE]] installations on certain Windows configurations (getting stuck on "Booting UBI file..."), has been finally fixed! If the installation has failed for you before, you can retry it using the updated version of our tool (use the iTunes method for now). | ||
* {{#dateformat:2012-01-02}} - There have been some problems with the latest release. A hotfix release ([[EmCORE_Releases/r859|r859]]) has been published to fix some of these problems. | * {{#dateformat:2012-01-02}} - There have been some problems with the latest release. A hotfix release ([[EmCORE_Releases/r859|r859]]) has been published to fix some of these problems. [[Nano 2G]] users are advised to upgrade. See the [[EmCORE_Releases/r859|release details page]] for more information. | ||
* {{#dateformat:2012-01-01}} - A new release <s>([[EmCORE_Releases/r855|r855]])</s> is out! It includes a couple of new features, several bugfixes and a new bootmenu theme! More information on the <s>[[EmCORE_Releases/r855|release details page]]</s>. | * {{#dateformat:2012-01-01}} - A new release <s>([[EmCORE_Releases/r855|r855]])</s> is out! It includes a couple of new features, several bugfixes and a new bootmenu theme! More information on the <s>[[EmCORE_Releases/r855|release details page]]</s>. | ||
* {{#dateformat:2011-04-25}} - The [[emCORE]] kernel now runs on the iPod Touch 2G as well, thanks to the help of kleemajo. This is of course not a fully functional port yet, but we'll see how it continues. It's about the same state as the | * {{#dateformat:2011-04-25}} - The [[emCORE]] kernel now runs on the iPod Touch 2G as well, thanks to the help of kleemajo. This is of course not a fully functional port yet, but we'll see how it continues. It's about the same state as the [[Nano 4G]] now. /7 | ||
* {{#dateformat:2011-03-25}} - [[emCORE]] is replacing [[emBIOS]] completely now. Therefore [[emBIOS]] will be deprecated software as of now! All emBIOS users are advised to upgrade to emCORE including people using iLoader 0.2.2 or less. More detailed update instructions will follow! | * {{#dateformat:2011-03-25}} - [[emCORE]] is replacing [[emBIOS]] completely now. Therefore [[emBIOS]] will be deprecated software as of now! All emBIOS users are advised to upgrade to emCORE including people using iLoader 0.2.2 or less. More detailed update instructions will follow! | ||
* {{#dateformat:2011-01-08}} - The Rockbox port for the iPod Classic is slowly getting usable. Most of the blocking issues have been fixed. The first-generation 160GB model still doesn't work, and some people are experiencing slightly garbled display contents. | * {{#dateformat:2011-01-08}} - The Rockbox port for the iPod Classic is slowly getting usable. Most of the blocking issues have been fixed. The first-generation 160GB model still doesn't work, and some people are experiencing slightly garbled display contents. | ||
| Line 44: | Line 51: | ||
* {{#dateformat:2010-08-13}} - [[emBIOS]] is continually being improved and the next step is porting tools like [[iLoader]] to use it. | * {{#dateformat:2010-08-13}} - [[emBIOS]] is continually being improved and the next step is porting tools like [[iLoader]] to use it. | ||
* {{#dateformat:2010-08-06}} - The wiki has now been moved to www.freemyipod.org | * {{#dateformat:2010-08-06}} - The wiki has now been moved to www.freemyipod.org | ||
* {{#dateformat:2010-08-05}} - Recently we've been working on a hardware abstraction project called [[emBIOS]]. Follow development [ | * {{#dateformat:2010-08-05}} - Recently we've been working on a hardware abstraction project called [[emBIOS]]. Follow development [https://websvn.freemyipod.org/listing.php?repname=freemyipod&path=/embios/ here] | ||
* {{#dateformat:2010-08-03}} - We can now access the Nano 4G accelerometer. | * {{#dateformat:2010-08-03}} - We can now access the [[Nano 4G]] accelerometer. | ||
* {{#dateformat:2010-08-02}} - serpilliere managed to decrypt the NOR flash on the [[Nano 3G]]. | * {{#dateformat:2010-08-02}} - serpilliere managed to decrypt the NOR flash on the [[Nano 3G]]. | ||
* {{#dateformat:2010-08-01}} - serpilliere managed to access and dump the NOR flash on the [[Nano 3G]]. This code could possibly work on the Classics. | * {{#dateformat:2010-08-01}} - serpilliere managed to access and dump the NOR flash on the [[Nano 3G]]. This code could possibly work on the Classics. | ||
* {{#dateformat:2010-07-27}} - The server got zapped by lightning but a new one was up and running within a day. | * {{#dateformat:2010-07-27}} - The server got zapped by lightning but a new one was up and running within a day. | ||
* {{#dateformat:2010-02-23}} - We can now execute code on everything besides the [[Nano 5G]]! Minimalistic iBugger working on [[Nano 3G]]! | * {{#dateformat:2010-02-23}} - We can now execute code on everything besides the [[Nano 5G]]! Minimalistic iBugger working on [[Nano 3G]]! | ||
* {{#dateformat:2009-11-01}} - iBugger core v0.1 successfully running on [[Nano 4G]]! [ | * {{#dateformat:2009-11-01}} - iBugger core v0.1 successfully running on [[Nano 4G]]! [https://img217.imageshack.us/img217/4122/img0969.jpg] | ||
--> | --> | ||
Follow [ | Follow [https://twitter.com/freemyipod our Twitter feed] to get status updates automatically. See the [[Status]] page for more detailed information. Check our [[Special:Code/freemyipod|SVN activity]] page for the latest changes to our source code. | ||
{| cellspacing="3" width="100%" | {| cellspacing="3" width="100%" | ||
| Line 114: | Line 121: | ||
** [[Nano 6G]] | ** [[Nano 6G]] | ||
** [[Nano 7G]] | ** [[Nano 7G]] | ||
** [[Classic | ** [[Classic 6G]] | ||
* [[Chronology]] | * [[Chronology]] | ||
* [[S5L8700 datasheet]] | * [[S5L8700 datasheet]] | ||
Latest revision as of 23:50, 4 January 2026

This is the wiki for the freemyipod project. Freemyipod is a project aimed at reverse-engineering non-iOS iPods (all models other than the Touch) and creating tools and documentation so that other people can port alternative firmwares to them such as Rockbox or Linux. Freemyipod is a relaunch of Linux4nano.
FAQ
What can I do with my iPod nano (2nd generation), iPod classic (6th generation) or older iPods?
There's an upstream Rockbox port for these devices. Go use that.
What can I do with my iPod nano (3rd generation) or newer?
Not much (yet) unless you're an embedded developer :).
On the iPod nano (3rd generation), iPod nano (4th generation) and iPod nano (5th generation), we have a stable tethered exploit (wInd3x) which allows early, untethered and safe (no permanent modification) code execution. This in turn allows you to run U-Boot and an early Linux port or experiment with reverse-engineering/modifying the original firmware, retailOS.
On the iPod nano (6th generation), iPod nano (7th generation) and iPod shuffle (4th generation), a vulnerability in DFU_DNLOAD packet parsing code can be exploited with S5Late. It allows tethered code execution.
On the iPod nano (6th generation) and iPod nano (7th generation), a font parsing vulnerability (CVE-2010-1797) can be exploited with ipod_sun. It allows untethered code execution.
There's a set of earlier tooling (emCORE/emBIOS/iBugger) which was exploiting other vulnerabilities and was a lead-up to a port of Rockbox, but it's mostly abandoned.
Getting an account
Due to spambots, registration is closed. For an account contact User890104 or q3k.
Updates
- 2025-12-28 - Hug0 made a lightning talk at 39C3 on iPod Nano reverse engineering.
- 2025-12-26 - Some of us will be at 39C3 in Hamburg! Get in touch with q3k and/or Slackware if you're around!
- 2025-06-12 - Some of us will be at GPN23 in Karlsruhe! More info here. Let us know on IRC/Discord/Matrix if you're also there!
- 2024-12-25 - Some of us will be at 38C3 in Hamburg! Come say hi!
- 2024-12-16 - S5Late, a tethered iPod bootrom/DFU exploit for iPod nano (7th generation) (and possibly iPod nano (6th generation)), is released.
- 2023-12-28 - ipod_sun, a tool that enables code execution on the iPod nano (6th generation) and iPod nano (7th generation), is released.
- 2023-01-07 - A preliminary U-Boot port to the iPod nano (5th generation) has been developed.
Follow our Twitter feed to get status updates automatically. See the Status page for more detailed information. Check our SVN activity page for the latest changes to our source code.
Project infoReleased Software
|
Basic skillsReverse engineering results
Other guides |
HardwareExploiting |