JTAG
Some iPods seemingly have the ability to be debugged over JTAG. Here's some documentation on getting started.
Devices
| Device | Protocol | Location |
|---|---|---|
| Nano 2G | JTAG (memory locked out) | 30-pin connector, needs jumpers |
| Nano 5G | JTAG (memory locked out) | 30-pin connector, needs jumpers |
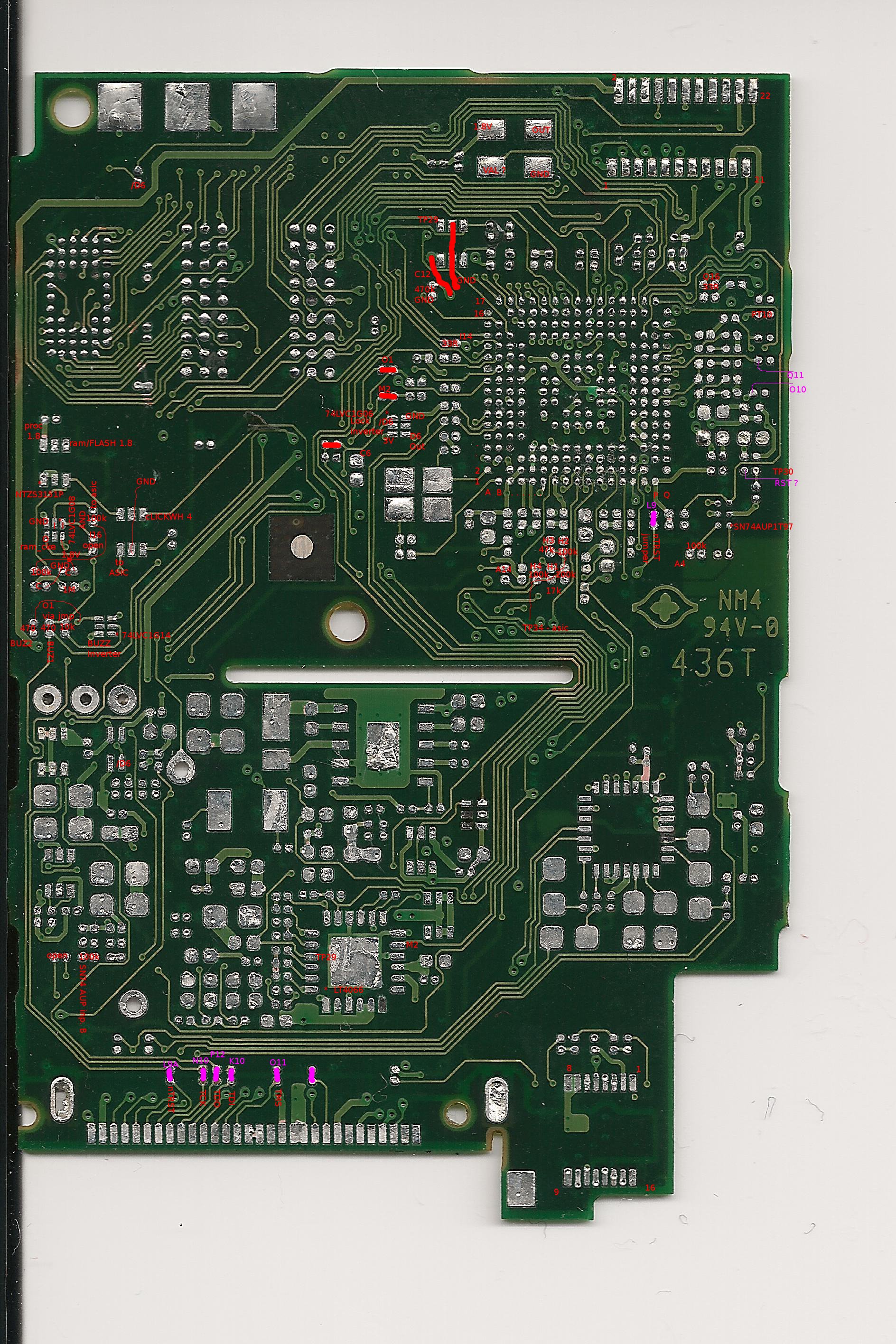
Nano 2G
The following pins carry 'classic' multi-wire JTAG on the Dock Connector:
| Pin Number | Function |
|---|---|
| 17 | TMS |
| 21 | TDI |
| 22 | TDO |
| 23 | TCK |
| 24 | nTRST |
In addition, the following pads need to be bridged on the logic board:
Nano 5G
The following pins carry 'classic' multi-wire JTAG on the Dock Connector:
| Pin Number | Function |
|---|---|
| 3 | RTCK (optional) |
| 5 | TDO |
| 9 | TDI |
| 14 | TCK |
| 17 | TMS |
In addition, the following 01005 footprints need to be populated with 0 ohm resistors (or bridged with a wire) on the logic board:
'Memory locked out' JTAG
Even though JTAG is accessible on the N2G/N5G, and the CPU core can be controlled over it, no memory is accessible anymore. In fact, it seems like the CPU core gets fully disconnected from the AHB bus any time JTAG is enabled. During the Nano 2G initial reverse engineering process low-level access to Dcache was used to dump memory. However, no method of re-establishing full memory access has yet been found.
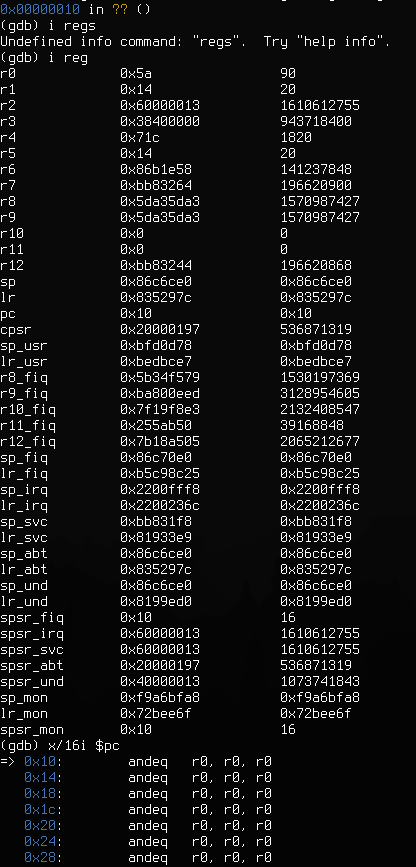
The above listing shows OpenOCD/GDB connected to a Nano 5G a while after it has been first scanned via JTAG. It seems to be stuck in a permanent 'data abort' handler loop, with some pretty trashed register values (although some of them are still in valid range for running the BootROM).
What has been attempted so far:
- Making sure the WDT isn't running.
- Opening all clock gates
- Writing to CHIPID in an attempt to 'demote' the devices à la iOS.
- Connecting while the device is in the BootROM.
- Using a fancy JTAG probe (Lauterbach)
- Writing to 0x3970_0104 (which seems to have three security write-only bits, two of which disable built-in AES keys, the third being unknown)
Other observations:
- The 'memory bus disconnection' seems to happen immediately after a JTAG chain scan, so this might be implemented as extra logic somewhere in the SoC that needs some magic TDI bits to be fed so it doesn't lock out the AHB bus (or whatever it does).
- This might just be a bug in openocd ARM11, or some quirk of the ARM1176 core (or SoC) in which caches break during debug access, but that seems unlikely.
- The implementation might be Samsung's 'SecureJTAG', as used in eg. the S5PC100. However, the S5L87xx does not seem to have eFUSE registers that would hold a key as described in this datasheet - or such a register hasn't yet been found. It is also unknown, given the key, how to actually send it over JTAG to unlock it.